File Security Articles
-

·
Why You Should Use IRM to Strengthen Document Security and Data Protection
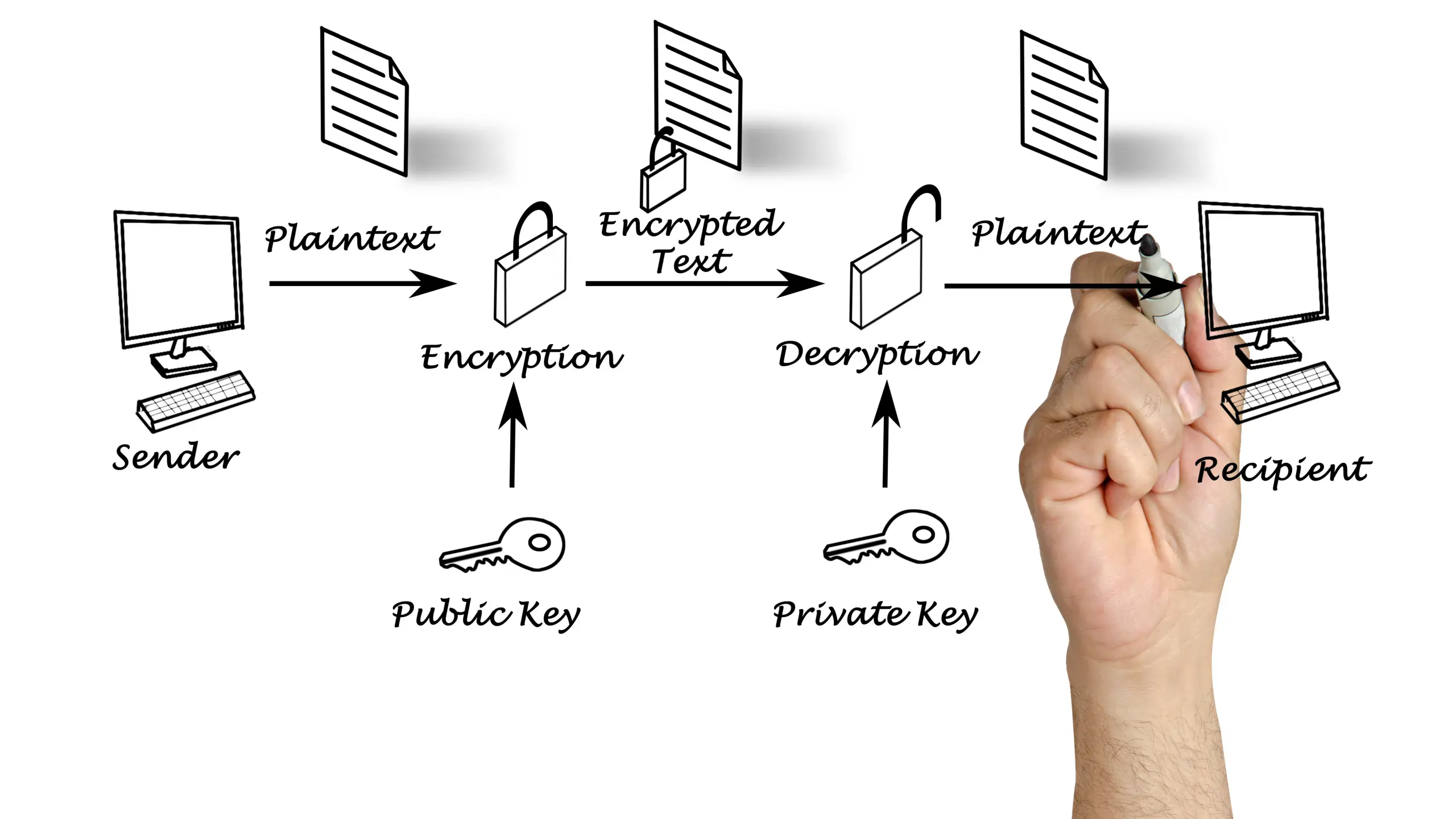
What is IRM Information Rights Management (IRM)—often linked with digital rights management (DRM)—is an advanced technology designed to protect sensitive information throughout its entire lifecycle. IRM applies identity-based access controls that define who can view, edit, print, or share a file, even after it has been downloaded. This makes it one of the most effective
-

·
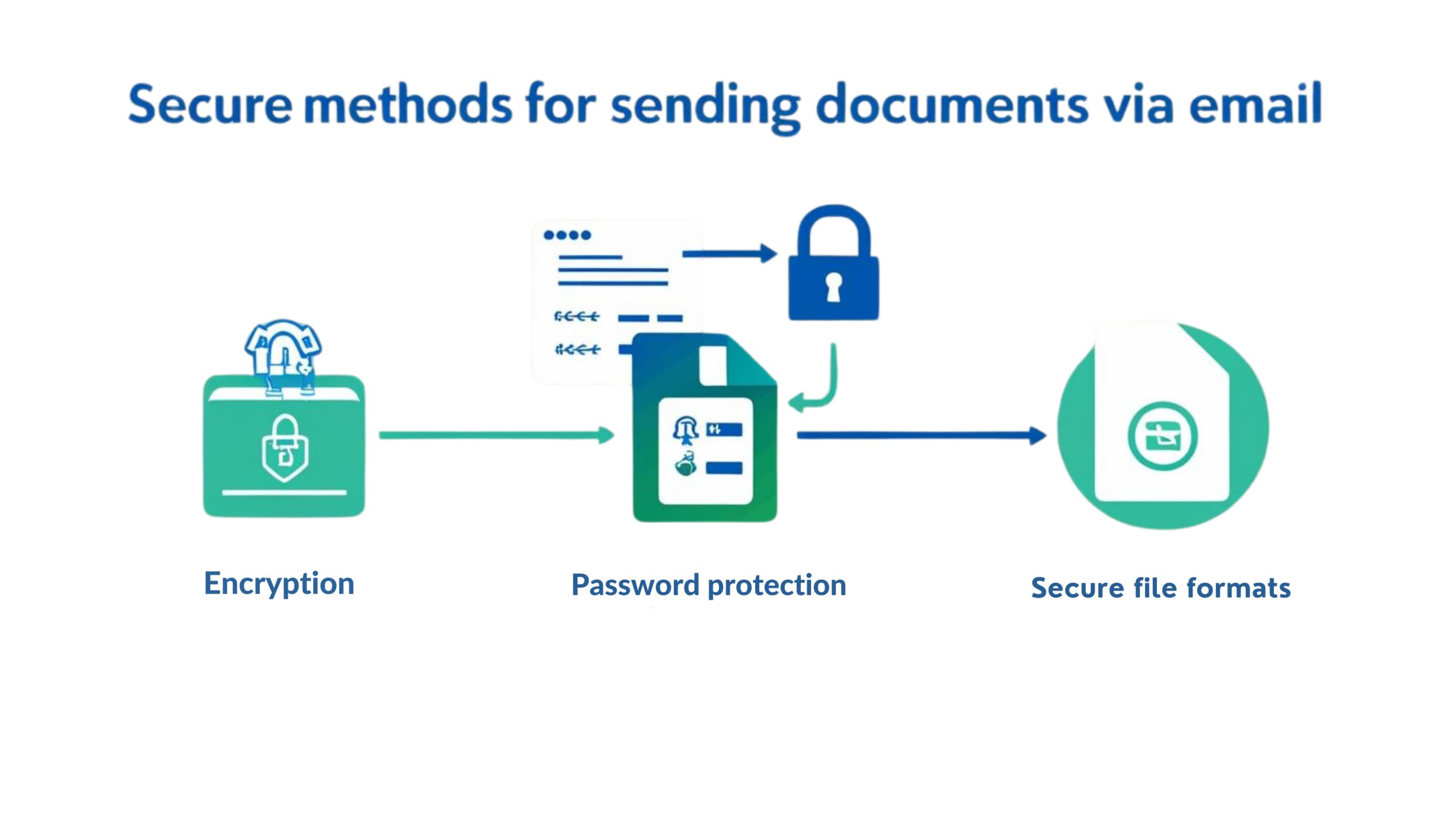
7 Powerful Tips to Send Documents Securely via Email
When you need to send documents securely via email, choosing the right protection methods is essential to keep your sensitive information safe from unauthorized access. Email is one of the most widely used tools for business communication. Its ubiquity, accessibility, and familiarity make it indispensable. Yet, when it comes to transmitting confidential or sensitive documents,
-

·
689Cloud Partners with the University of Economics Ho Chi Minh City (UEH) to Protect Online Lecture Videos
On September 18, 2025, The University of Economics Ho Chi Minh City (UEH) announced that they have 689Cloud Solutions, Ltd. (689Cloud) to deploy an online system that safeguards lecture videos using Digital Rights Management (DRM) technology. This marks the first time in Vietnam that a university applies a modern copyright protection solution for online educational
-

·
How to Handle Sensitive Information and Keep It Secure in the Cloud
How to Handle Sensitive Information is one of the most important topics for any organization working with cloud-based systems, and 689Cloud provides practical tools to secure this sensitive data effectively. This article breaks down: What counts as sensitive information in a business context Best practices for managing and securing it How 689Cloud provides a safer
-

·
Secure File Sharing: 13 Powerful Ways to Protect Your Company’s Data with 689Cloud
Secure File Sharing plays a critical role in protecting company data in today’s digital environment. Every time you browse the internet, use cloud storage, or communicate online, you leave behind digital breadcrumbs. While many online services appear to be free, the real cost is often your data. Even when you pay for a service, your
-

·
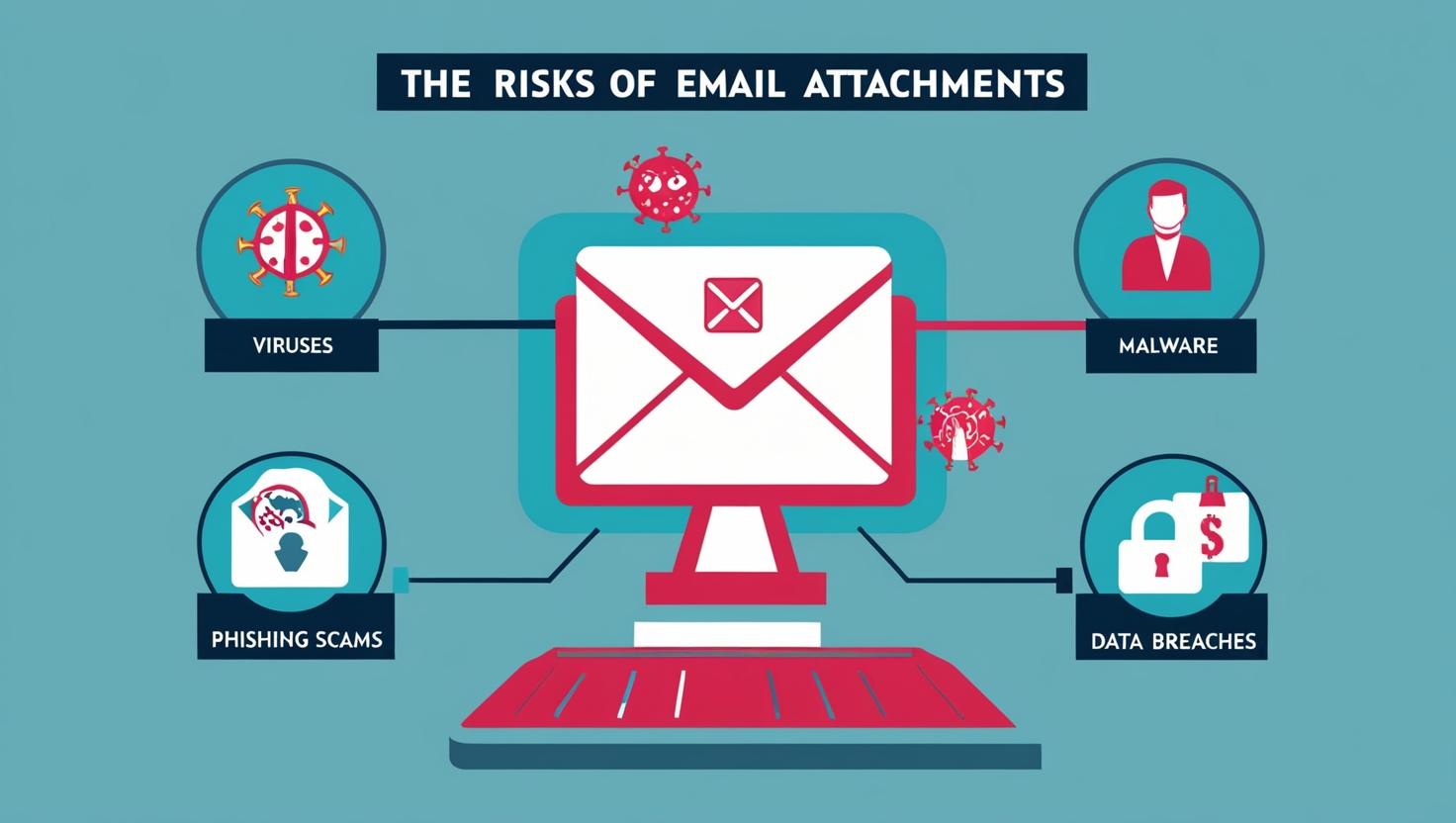
Secure Email Attachments: 3 common scenarios from email attachments
Protecting Confidential Documents Across Industries Secure email attachments are essential for protecting business communications in today’s digital environment. Whether you work in education, design, finance, or enterprise IT, your documents are valuable and vulnerable. Once an email is sent, the attached file can easily be forwarded, copied, downloaded, or even exposed to unauthorized users. Without
-

·
5 Common Mistakes When Sending Sensitive Data by Email
Why Sending Sensitive Data by Email Is a Serious Risk Sending sensitive data by email may seem convenient, but it exposes businesses to serious security risks if not handled properly. But for organizations handling sensitive data, such as legal contracts, financial statements, health records, and proprietary business information, email can also be a significant security
-

·
5 Critical Data Security Lessons from the Sushi Wars
In February 2024, Tokyo prosecutors convicted Kappa Sushi of stealing trade-secret data from rival Hama Sushi. A former Hama executive, after joining Kappa, secretly took a file of Hama’s cost and product plans and handed it to Kappa’s planning manager. As a result, Kappa gained an unfair edge in competition. The court ruled this was
-

·
4 Critical Risk Attachments Issues That Threaten Your Business Security
Why Sending Email Attachments Is Putting Your Business at Risk Email remains one of the most widely used tools for business communication — and one of the most common ways sensitive files are shared. But while email attachments are convenient, they also pose a serious risk to your organization’s data security. If you’re a CIO
-

·
Data Breach Prevention: How Content Security Could Have Averted the Fukuoka COVID-19 Patient Data Leak
Data breach incidents are on the rise and pose enormous risks to organizations’ security. In fact, IBM reports that the global average cost of a data breach reached $4.45 million in 2023. One notable example is the Fukuoka COVID-19 patient data leak: in January 2021 the Fukuoka Prefectural Government inadvertently exposed the personal information (names, location,
-

·
How to Share Internal Documents Securely – Document Security Best Practices 2025
Internal documents often include a company’s most sensitive information, from financial reports to proprietary research. Yet common sharing methods like email or USB drives leave these files vulnerable. In fact, studies show nearly 60% of organizations have been hit by attacks (like ransomware) when sharing data, and errors are frequent: one city employee once emailed
-

·
Serious Document & File Sharing Risks Companies Overlook
You’re Sharing Files All Wrong — Here’s How to Do It Right (and Securely) File sharing is critical to daily operations, whether it is sending pricing proposals, investor decks, or product roadmaps, most organizations rely on tools like email, Google Drive, or Dropbox to share documents quickly. But here’s the problem: the very tools that
-

·
Secure File Sharing and Document Security: Safeguarding Data from Insider Threats
In recent years, high-profile cases have shown how departing employees can turn into costly insider threats. For example, Tokyo police arrested a former SoftBank engineer accused of emailing confidential 4G/5G base-station designs from SoftBank to his new employer, Rakuten Mobile. SoftBank alleges the ex-employee used a personal email account on his last day to send
-

·
F1 IP Breach Controversy: How to Protect Your Company’s Intellectual Property
Formula One teams invest millions in R&D, making their intellectual property (IP) extremely valuable. Last year’s dispute between Red Bull Racing and Aston Martin illustrated just how high the stakes can be. An upgraded Aston car looked strikingly similar to Red Bull’s design, sparking accusations of copying. The FIA investigation ultimately cleared Aston Martin of