When you need to send documents securely via email, choosing the right protection methods is essential to keep your sensitive information safe from unauthorized access.
Email is one of the most widely used tools for business communication. Its ubiquity, accessibility, and familiarity make it indispensable. Yet, when it comes to transmitting confidential or sensitive documents, email is also one of the most vulnerable channels.
A single misstep—whether a data breach, misdirected message, or accidental attachment—can result in regulatory violations, reputational damage, and significant financial loss. One of the easiest ways to send documents securely via email is to encrypt the file before uploading it.
Whether you are sharing business contracts, employee records, financial data, or healthcare information, sending documents securely requires more than simply pressing “send.” It calls for a comprehensive security strategy that prioritizes:
- Encryption to protect documents in transit and at rest
- Access control to verify and limit who can view files
- Traceability to ensure accountability and compliance
- Control after sending such as remote revocation and limiting copying and printing
This guide explains the building blocks of document security, their strengths and limitations, and how 689Cloud SecureMail brings them together in a practical, easy-to-use solution.
What is Document Security?
At its core, document security ensures that sensitive files can only be accessed by authorized parties—and remain protected throughout their lifecycle.
When most people hear the term, they think of encryption. While encryption is critical, it is not enough on its own. To fully protect sensitive data, a layered approach is necessary.
Why Encryption Alone is Insufficient
One of the most effective ways to send documents securely via email is to encrypt your files before sending them. Encryption ensures that only the intended recipient can access the content. For example:
- During transmission, encryption prevents hackers from intercepting and reading files.
- On servers, encryption protects documents if storage systems are compromised.
However, once the recipient decrypts the file, the sender’s control ends. The recipient can forward, copy, or save the document to unsecured locations. If their device is hacked, the document is also exposed.
Key takeaway: Encryption is essential, but it must be combined with control after sending for full lifecycle protection.
The Role of Access Control
Access control verifies the identity of recipients before allowing them to open files. Common methods include:
- Passwords – a basic but often weak control, since passwords can be guessed or shared.
- Two-Factor Authentication (2FA) – a stronger option that requires both something the user knows (password) and something they have (e.g., a mobile code).
Platforms like SharePoint, Box, and Dropbox make use of these controls, which explains their popularity in business settings.
But access control has a major limitation: once the document is downloaded, the sender no longer has control.
View-Only Restrictions
To reduce risks, many file-sharing services provide view-only modes, which prevent recipients from downloading files. This significantly strengthens security because the document never leaves the owner’s control.
Advanced view-only systems such as SecureMail go further by:
- Disabling copy-and-paste
- Preventing retrieval from browser caches
- Blocking screen capture and print-to-file options
- Applying dynamic watermarks to discourage leaks and identify violators
While view-only restrictions enhance protection, they must be robust and complemented by encryption, access control, and traceability.
Traceability: The Audit Trail
Regulators increasingly demand that organizations keep an audit trail showing:
- Who accessed a document
- When they accessed it
- Where they accessed it from
For view-only solutions, detailed logs can capture this information, providing accountability and compliance evidence.
For downloadable files, however, tracking usually ends once the file is saved. At that point, the sender has no visibility or control. Maintaining control after downloading greatly improves the traceability of a document.
Information Rights Management (IRM)
IRM combines the strengths of multiple security methods into one framework. It provides:
- Encryption at rest and in transit
- Access control including fine-grained permissions (view-only, no print, no copy, etc.)
- Tracking of all document interactions, even after distribution
With IRM, documents remain encrypted on the recipient’s system and are only decrypted temporarily while in use. Some solutions also offer secure online viewers for non-downloadable files.
While IRM is powerful, adoption has been slow because:
- Many solutions require expensive infrastructure
- Recipients often need to install specialized software
- Complexity discourages everyday use
As a result, organizations still frequently rely on email attachments or general-purpose file-sharing tools for sensitive documents—despite their limitations.
The Importance of Convenience
No matter how strong a security system is, it will fail if users find it too cumbersome. Common barriers include:
- Having to encrypt files in a separate application before emailing them
- Requiring recipients to install software just to open a file
- Overly complex authentication steps that frustrate users
A practical solution must balance security and convenience—protecting documents without disrupting business workflows.
Introducing 689Cloud SecureMail
689Cloud SecureMail is an add-in for Gmail and Microsoft Outlook that integrates enterprise-level document security directly into the email workflow. Tools like SecureMail make it easier to send documents securely via email by offering built-in encryption, access control, and file tracking. Unlike traditional encryption tools, SecureMail uses IRM technology to combine:
- Encryption
- Access control
- View-only capability
- Post-download control and protection
- Comprehensive tracking
How it Works:
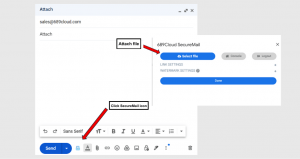
- Install the SecureMail Add-in – The add-in is available for free on the Google Chrome Store for Gmail, and on Microsoft AppSource for Outlook.
-
Attach as usual – The sender clicks on the SecureMail icon and attaches files through the SecureMail add-in, just like a normal email attachment.

- Set Permissions – Permissions such as downloading and printing can be set.
- Automatic encryption – The files are encrypted and uploaded securely to the cloud.
- Secure link – A link to the document is embedded in the email body.
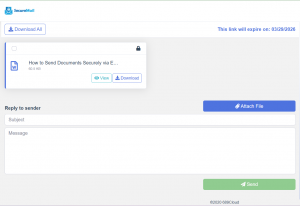
- Recipient authentication – The recipient clicks the link and is verified via their email address and a one-time PIN (OTP).
-
Controlled access – Based on the sender’s permissions, the recipient can either:
. View the file securely in their browser (without downloading), or
. Download it with tracking and restrictions still in place.
-
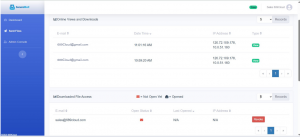
Track and Manage – The sender can check who has accessed sent files, stop access, and revoke access to downloaded files through the SecureMail Dashboard.

Benefits:
- Simplicity for senders – No extra steps beyond attaching a file.
- Ease for recipients – No special software required, access via browser.
- Strong security – Encryption, access control, traceability, and post-sending control in one seamless solution.
Conclusion: Consider all the Factors when Sending Sensitive Documents
As we have discussed, just password protecting the file is not enough to securely send a document by email. All factors including encryption, access control, tracking, and protection after a document has been downloaded need to be considered. Email is still an easy and ubiquitous way to send documents, and with the SecureMail add-in, it can be done securely too. Pricing and availability are here.
SecureMail Frequently Asked Questions (FAQ)
-
Do recipients need to install any software?
No. They just authenticate via their email and OTP. Documents open securely in the browser. Downloadable PDF files can be opened with Adobe Acrobat Reader. -
Can recipients forward the email?
Yes, but forwarded recipients cannot open the file unless the sender grants them access. -
What happens if someone screenshots the document?
Print Screen and screen capture tools are disabled. Dynamic watermarks also deter photos. -
Can I revoke a file after sending it?
Yes. At any time via the SecureMail dashboard. -
What file formats are supported?
Common business file types like PDF, Word, Excel, PowerPoint, and images. -
What happens if the download option is disabled?
Recipients can only view online. They cannot download, copy, or extract the content.
By: Hiro Kataoka