-
How to Send Large Files Securely Without Compromising Quality or Privacy
In enterprise environments, large file transfers are an everyday need — from detailed project proposals and raw datasets to high-resolution design assets and compliance documents. Yet transferring these files can present serious challenges, especially when privacy and performance are key concerns. For CIOs and CISOs, the issue goes beyond basic file sharing. You’re tasked with…
-

How to Handle Sensitive Information and Keep It Secure in the Cloud
Every organization handles sensitive data—whether it’s internal financial reports, client contracts, product roadmaps, or employee records. For CIOs and CISOs, protecting this information isn’t just about compliance; it’s about trust, operational integrity, and business continuity. This article breaks down: What counts as sensitive information in a business context Best practices for managing and securing it…
-

13 Effective Ways to Protect Your Company’s Data and Ensure Secure File Sharing
Your personal and business data is a valuable asset—and it’s constantly under threat. Every time you browse the internet, use cloud storage, or communicate online, you leave behind digital breadcrumbs. While many online services appear to be free, the real cost is often your data. Even when you pay for a service, your information may…
-

Why Secure Email Attachments Matter
Protecting Confidential Documents Across Industries Email remains one of the most common ways to share files in business today. But traditional email attachments pose serious security risks, especially when those files contain confidential, proprietary, or personally identifiable information. Whether you work in education, design, finance, or enterprise IT, your documents are valuable and vulnerable. Once…
-

Support Center’s SecureMail
Versions of Microsoft Outlook Supported: Microsoft 365: Web, Windows10, MacOS. Microsoft Exchange 2016, 2019: Web, Window10, Window11, MacOS. Versions of Google Gmail Supported: Gmail running in Google Chrome on Windows10, Window11 and MacOS. Start With Outlook Start With Gmail
-

·
5 Common Email Mistakes That Put Sensitive Data at Risk — And How to Avoid Them
In today’s digital-first business environment, email remains one of the most widely used tools for communication and file sharing. But for organizations handling sensitive data, such as legal contracts, financial statements, health records, and proprietary business information, email can also be a significant security risk. Cybercriminals constantly seek new ways to exploit email vulnerabilities. Whether…
-

·
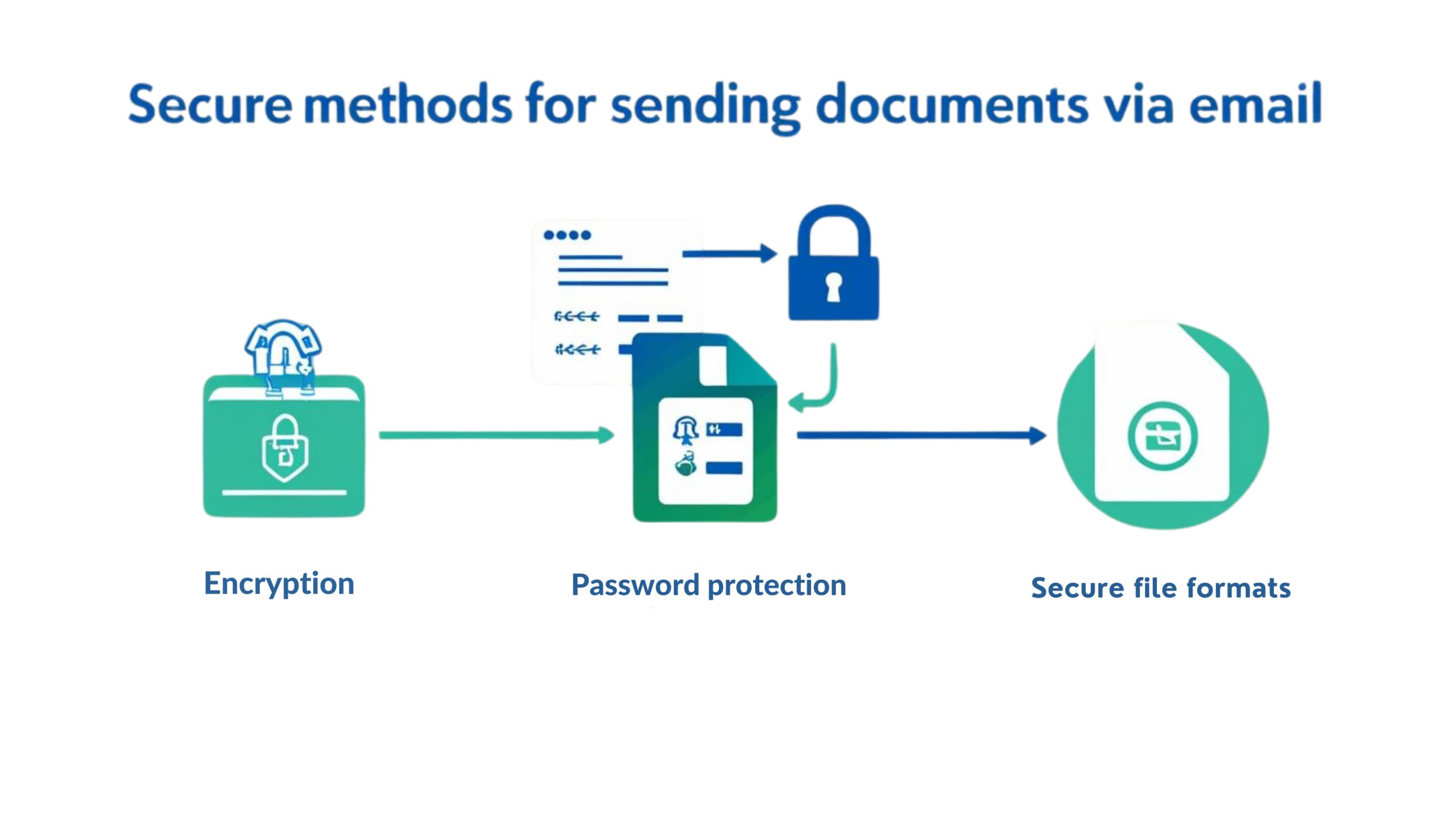
How to Send Documents Securely via Email
Email remains one of the most widely used tools for business communication, but when it comes to sending confidential documents, it’s also one of the most vulnerable. From data breaches to accidental leaks, one simple misstep in document transmission can lead to regulatory issues, reputational damage, or financial loss. Whether you’re sharing sensitive business contracts,…
-

·
The Sushi Wars and Data Security
On February 26, 2024, the Tokyo District Court convicted Kappa Sushi of violating the Unfair Competition Prevention Act (trade secret infringement) for Kappa Sushi’s fraudulent use of Hama Sushi’s trade secrets. This incident occurred in 2020 when a former executive, who changed his job from Hama Sushi to Kappa Sushi, obtained a file containing trade…
-

·
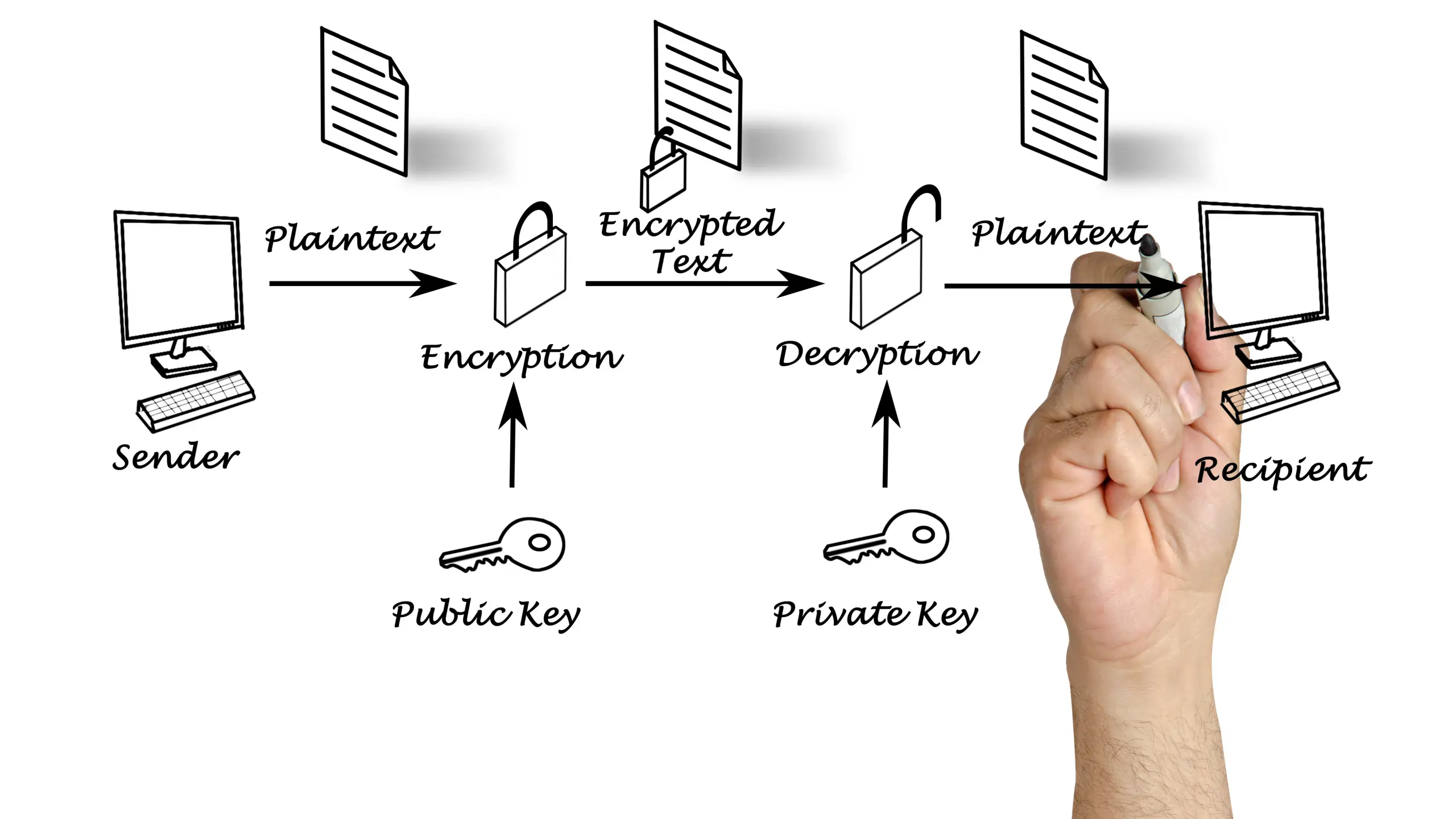
What is IRM, and Why You Should Use It?
What is IRM, and Why You Should Use It Information Rights Management (IRM) is a combination of technologies that control and manage access to sensitive information or digital content. The reasons for using IRM are to safeguard sensitive data, prevent unauthorized access, and control how authorized users can use that information. Compared to password protection…
-

·
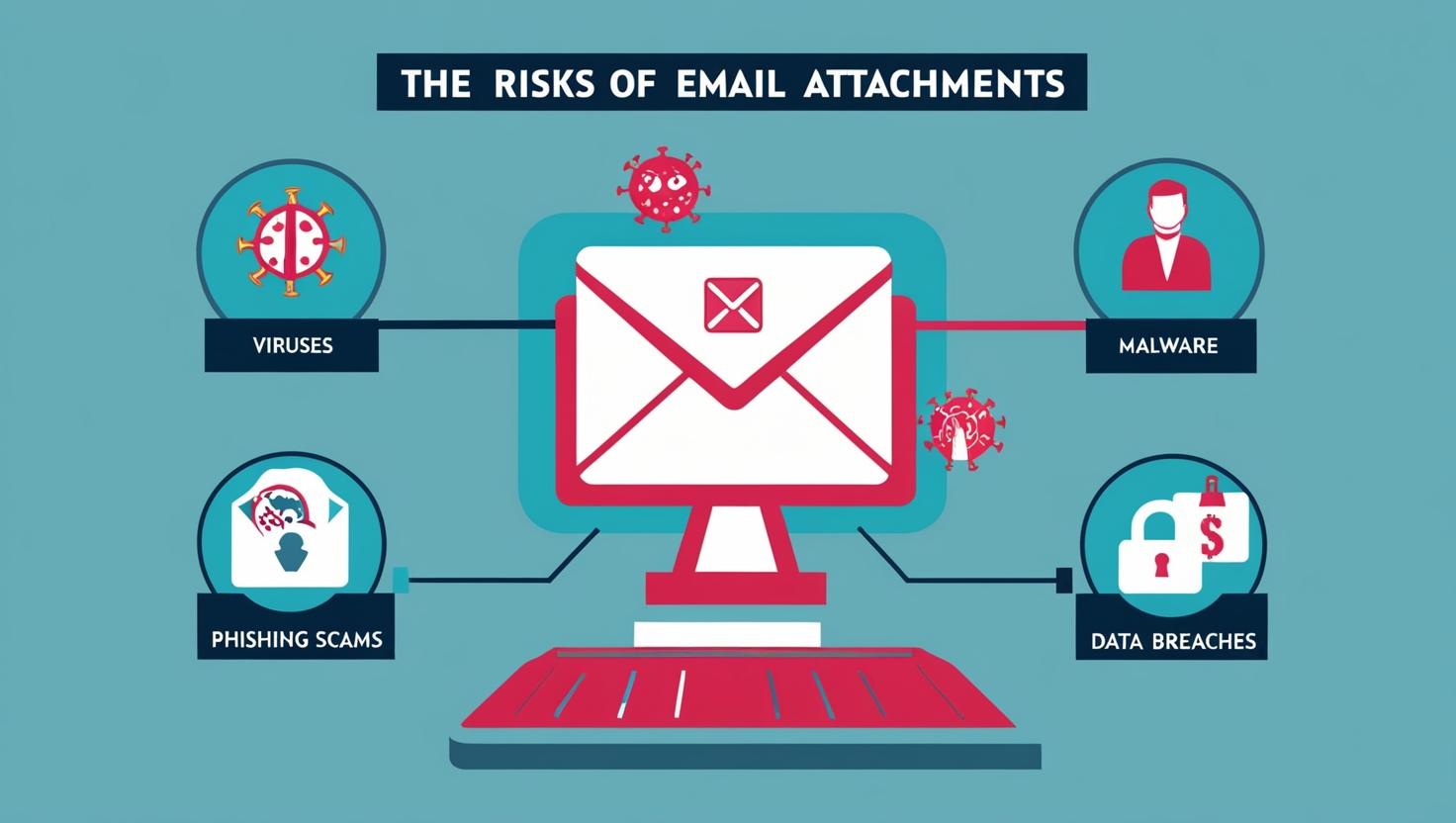
The Risks Of E-Mail Attachments
Why Sending Email Attachments Is Putting Your Business at Risk (And What to Do Instead) Email remains one of the most widely used tools for business communication — and one of the most common ways sensitive files are shared. But while email attachments are convenient, they also pose a serious risk to your organization’s data…